Perhaps you received this email from Elementor yesterday regarding a critical security vulnerability discovered in Elementor Pro versions 3.11.6? This vulnerability can be exploited if WooCommerce is also installed on your website. it contained the following message:
Email message from Elementor
The message below is translated from English into Dutch.
Dear customer,
We would like to inform you about a critical security vulnerability discovered in Elementor Pro versions 3.11.6 and earlier versions. This vulnerability can be exploited if WooCommerce is also installed on your website.
To protect your website and ensure security, we strongly recommend that you update your Elementor Pro plugin to the latest version immediately. Follow these simple steps to complete the update:
- Log in op uw WordPress Admin Dashboard.
- Go to ‘Plugins’ in the left menu.
- Find Elementor Pro or PRO Elements in the list of installed plugins.
- Click the ‘Update Now’ button to start the update process.
Once the update is completed, your website will be protected from the security vulnerability and you can continue using Elementor Pro with confidence. If you encounter any problems or have any questions during the update process, please feel free to contact our support team. We are ready to help you and ensure that your website remains secure.
We apologize for any inconvenience this may cause and appreciate your prompt attention to this matter. Keeping your website secure is our top priority and we continue to work hard to address any security issues and keep you informed.
Thank you for choosing our services and for your cooperation in maintaining a safe online environment.
Kind regards, Dream-Theme team.
What does this vulnerability mean?
When Elementor Pro is installed on a site with WooCommerce enabled, the component “elementor-pro/modules/woocommerce/module.php” is loaded, which logs a number of AJAX actions:
/**
* Register Ajax Actions.
*
* Registers ajax action used by the Editor js.
*
* @since 3.5.0
*
* @param Ajax $ajax
*/
public function register_ajax_actions( Ajax $ajax ) {
// `woocommerce_update_page_option` is called in the editor save-show-modal.js.
$ajax->register_ajax_action( 'pro_woocommerce_update_page_option', [ $this, 'update_page_option' ] );
$ajax->register_ajax_action( 'pro_woocommerce_mock_notices', [ $this, 'woocommerce_mock_notices' ] );
}
One of them is pro_woocommerce_update_page_option, which is used by Elementor’s built-in editor. It calls update_option, a function that can be used to change WordPress options in the database, with two user inputs:
/**
* Update Page Option.
*
* Ajax action can be used to update any WooCommerce option.
*
* @since 3.5.0
*
* @param array $data
*/
public function update_page_option( $data ) {
update_option( $data['option_name'], $data['editor_post_id'] );
}
This feature is intended to allow the administrator or shop manager to update some specific WooCommercerce options, but user input is not validated and the feature lacks a capacity check to limit access to a privileged user.
Elementor uses its own AJAX handler to manage most of its AJAX actions, including pro_woocommerce_update_page_option, with the global elementor_ajax action. This is located in the “elementor/core/common/modules/ajax/module.php” script of the free version (which is required to run Elementor Pro):
/**
* Handle ajax request.
*
* Verify ajax nonce, and run all the registered actions for this request.
*
* Fired by `wp_ajax_elementor_ajax` action.
*
* @since 2.0.0
* @access public
*/
public function handle_ajax_request() {
if ( ! $this->verify_request_nonce() ) {
$this->add_response_data( false, esc_html__( 'Token Expired.', 'elementor' ) )
->send_error( Exceptions::UNAUTHORIZED );
}
...
We can see that it contains a nonce check that could potentially prevent bad actors from exploiting the vulnerability. But the nonce and all JS code associated with it is loaded via the admin_enqueue_scripts hook in “elementor/core/common/app.php”:
add_action( 'admin_enqueue_scripts', [ $this, 'register_scripts' ] );
So it leaks into the source of the page to all logged in users:
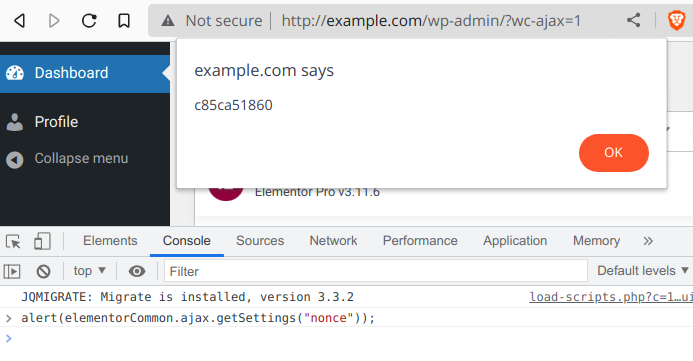
An authenticated attacker could exploit the vulnerability to create an administrator account by enabling registration (users_can_register) and setting the default role (default_role) to “administrator”, changing the administrator email address (admin_email), or, as shown below, redirect all traffic to an external malicious website by changing the site URL, among other things:
MariaDB [example]> SELECT * FROM `wp_options` WHERE `option_name`='siteurl'; +-----------+-------------+------------------+----------+ | option_id | option_name | option_value | autoload | +-----------+-------------+------------------+----------+ | 1 | siteurl | https://slechteurl.nl| yes | +-----------+-------------+------------------+----------+ 1 row in set (0.001 sec)
Because the vulnerable component requires WooCommerce to be installed, an unauthenticated user can create a WooCommerce customer account, log in, and also exploit the vulnerability (WooCommerce customers can gain access to the backend by adding wc-ajax=1 to the query , for example https://example.com/wp-admin/?wc-ajax=1).
The vulnerability was discovered and reported to the authors on March 18, 2023, and a new version 3.11.7 was released on March 22, 2023.
Solution for the WP Provider
You don’t have to do anything if you use Managed Hosting via WP Provider, your Elementor Pro version 3.11.6 has been updated to the latest version.
Solution for non WP Provider users
The solution is to update to the newer Elementor Pro version 3.11.7 as soon as possible. Always check whether newer versions are compatible with the plugins and themes used.
If you currently host multiple WordPress websites and you do not do this through us, you can use one of our WordPress bash scripts which can be found on our Github page.
For example, use our bash script to see which websites are still running on 3.11.6: https://github.com/wpprovider/bash-scripts/blob/main/check-elementor-pro-version.sh
And to make it even easier, the following bash script to also update these websites to 3.11.7: https://github.com/wpprovider/bash-scripts/blob/main/update-specific-elementor-pro- version.sh
Learn more about this vulnerability directly from the source.



